Notice: Trying to access array offset on value of type null in /srv/pobeda.altspu.ru/wp-content/plugins/wp-recall/functions/frontend.php on line 698
In addition to addressing known threats, identifying and analyzing risks is important to minimize successful cyber attacks. Cyber law helps protect users from harm by enabling the investigation and prosecution of online criminal activity. For example, organized crime syndicates using the internet to distribute illegal substances may face prosecution under cyber laws. While cyber crime impacts the global community, the adoption of cyber crime legislation varies among countries. Some countries amend their existing national codes with legislative language on cyber crime. Seventy-two percent of countries have cyber laws, 9% have draft legislation, and 18% have no cyber laws, according to 2019 data from the United Nations. What is cyber law in different countries? Security Tools: Security tools help organizations prevent and defend against cyber crime, enabling a quick recovery from damages related to a cyber attack. Denial of service attack is one of the factor that can hamper the availability of information. The Android Browser included with Android 4.0 and older is still vulnerable to the FREAK attack. Singaporean Bachelor and Bachelor Honours degrees are typically accepted GPA 3.0 out of 4.0 or 3.8 out of 5.0 or II (upper) — Second Class (Upper) Honours equivalent to a UK 2:1 (second-class upper) Honours Bachelor degree and GPA 2.5 out of 4.0 or 3.3 out of 5.0 or II (lower) — Second Class (lower) Honours equivalent to a UK 2:2 (second-class lower) Honours Bachelor degree
In today’s cloud-based work environment, third-party cloud-based vendors provide comprehensive, budget-friendly security solutions. In the US, for example, the controversial USA Patriot Act of 2001, and the revelation by Edward Snowden in 2013 that the National Security Agency harvests the personal data of the general public, brought these issues to wide public attention. Use an attack surface monitoring solution to detect internal and third-party vulnerabilities increasing data breach risks. It introduced a differentiated approach, such as identifying existing and emerging cybersecurity threats, finding and plugging existing cyber vulnerabilities and apprehending those trying to access federal information systems. Threats, attacks, and vulnerabilities: This includes social engineering attacks, newer denial-of-service (DDoS) attacks, and vulnerabilities found in internet of things (IoT) and embedded devices. We offer a global ecosystem of partners to better detect, investigate and respond to security threats, and ensure compliance with the federal government. The new department consisted primarily of components transferred from other Cabinet departments because of their role in homeland security, such as the Coast Guard, the Federal Protective Service, U.S. U.S. Secretary of State Hillary Clinton has said that, «The countries that threaten regional and global peace are the very places where women and girls are deprived of dignity and opportunity»
You can take online courses through institutions like Coursera, Khan Academy, edX, Udemy, and more. The President’s Cybersecurity National Action Plan (CNAP) is the capstone of more than seven years of determined effort by this Administration, building upon lessons learned from Cybersecurity advanced-level Jobs Singapore trends, threats, and intrusions. Free access to select CompTIA online courses for educational institutions during the Spring and Summer 2020 semesters — learn more. Access control — the selective restriction of access to a place or other resource. Authorization — the function of specifying access rights/privileges to resources related to information security and computer security in general and to access control in particular. United Nations. «Hunger and food security». Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g. freedom from want); as the presence of an essential good (e.g. food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g. a secure telephone line); as containment (e.g. a secure room or cell); and as a state of mind (e.g. emotional security). Food and Agriculture Organization (2013). «Greater focus on soil health needed to feed a hungry planet». Another problem of perception is the common assumption that the mere presence of a security system (such as armed forces, or antivirus software) implies security
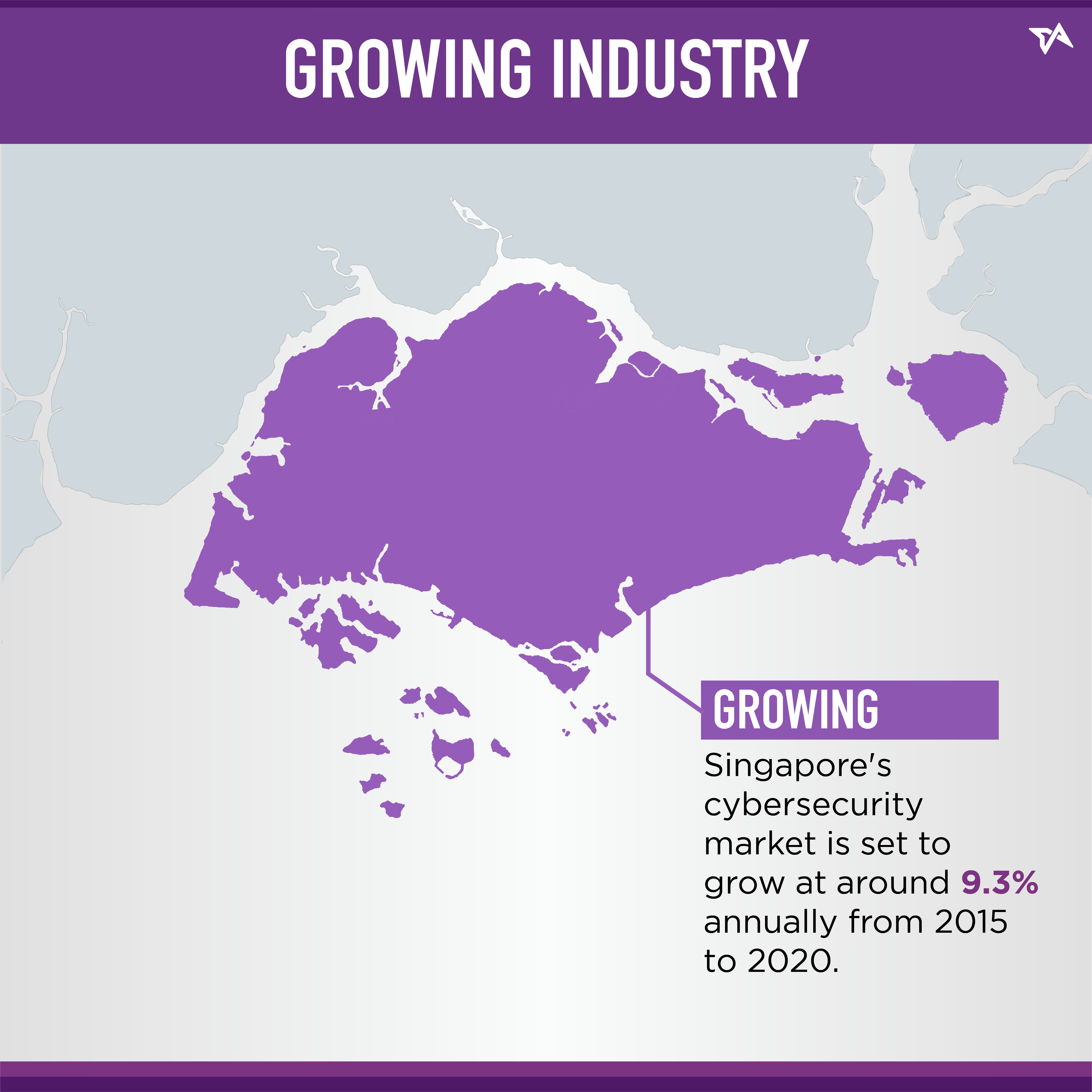 Malaysian Bachelor degrees from MQA Tier 4 institutions are typically accepted with GPA 3.2 equivalent to a UK 2:1 (second-class upper) Honours Bachelor degree GPA 2.8 equivalent to a UK 2:2 (second-class lower) Honours Bachelor degree. This degree should be a consideration for students that intend to invest their careers in cybersecurity research or academia. President Obama said the «cyber threat is one of the most serious economic and national security challenges we face as a nation» and that «America’s economic prosperity in the 21st century will depend on cybersecurity». Topics covered include: overview of network security; basics of cryptography; threat models; authentication and authorization mechanisms and standards; public key infrastructure; electronic mail security; network layer security; transport layer and web security; packet filtering, firewalls, intrusion detection, and virtual private networks; recent topics in network security. The connection is reliable (or has integrity) because each message transmitted includes a message integrity check using a message authentication code to prevent undetected loss or alteration of the data during transmission. It enhances privacy and saves data on the cloud, making it excess able from any device but needs correct authentication. Technical courses on specialized or emerging topics offered on a periodic or as-needed basis such as the semantic web, data privacy, forensics, or malware analysis
Malaysian Bachelor degrees from MQA Tier 4 institutions are typically accepted with GPA 3.2 equivalent to a UK 2:1 (second-class upper) Honours Bachelor degree GPA 2.8 equivalent to a UK 2:2 (second-class lower) Honours Bachelor degree. This degree should be a consideration for students that intend to invest their careers in cybersecurity research or academia. President Obama said the «cyber threat is one of the most serious economic and national security challenges we face as a nation» and that «America’s economic prosperity in the 21st century will depend on cybersecurity». Topics covered include: overview of network security; basics of cryptography; threat models; authentication and authorization mechanisms and standards; public key infrastructure; electronic mail security; network layer security; transport layer and web security; packet filtering, firewalls, intrusion detection, and virtual private networks; recent topics in network security. The connection is reliable (or has integrity) because each message transmitted includes a message integrity check using a message authentication code to prevent undetected loss or alteration of the data during transmission. It enhances privacy and saves data on the cloud, making it excess able from any device but needs correct authentication. Technical courses on specialized or emerging topics offered on a periodic or as-needed basis such as the semantic web, data privacy, forensics, or malware analysis