Notice: Trying to access array offset on value of type null in /srv/pobeda.altspu.ru/wp-content/plugins/wp-recall/functions/frontend.php on line 698
There are a few manner ins which hackers can access to a victim’s computer system to release ransomware. One way is through phishing e-mails. Hackers will send e-mails that appear like they are from a genuine source, such as a business or a bank. The e-mail will typically include a link that, when clicked, will take the victim to a harmful site that will infect their computer system with ransomware.
The e-mail will typically include a link that, when clicked, will take the victim to a harmful site that will infect their computer system with ransomware.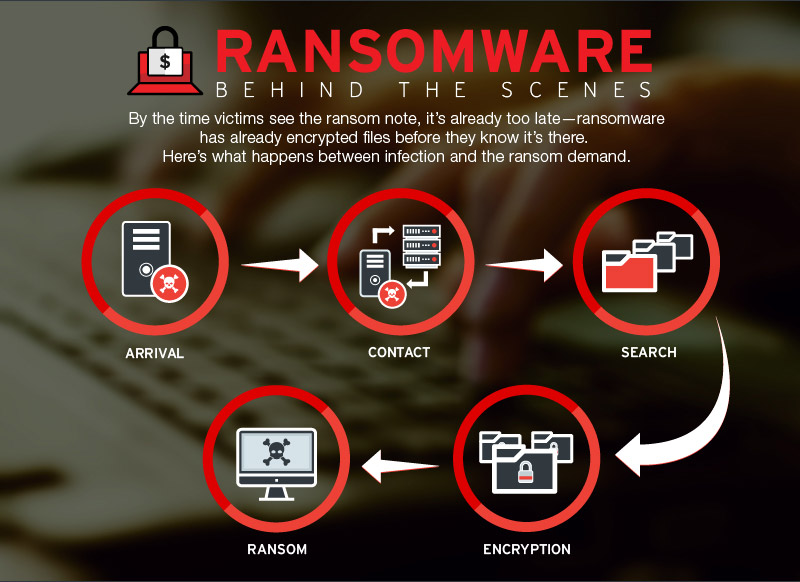 Another method is through Drive-By Downloads. This is where hackers will make use different types of ransomware (blog post from linktr.ee) vulnerabilities on sites to inject harmful code that will instantly download and ransomware is malware set up ransomware on the victim’s computer.
Another method is through Drive-By Downloads. This is where hackers will make use different types of ransomware (blog post from linktr.ee) vulnerabilities on sites to inject harmful code that will instantly download and ransomware is malware set up ransomware on the victim’s computer. When the ransomware is installed, it will encrypt the victim’s files and require a ransom be paid in order for the files to be decrypted and accessed once again.
When the ransomware is installed, it will encrypt the victim’s files and require a ransom be paid in order for the files to be decrypted and accessed once again.