Notice: Trying to access array offset on value of type null in /srv/pobeda.altspu.ru/wp-content/plugins/wp-recall/functions/frontend.php on line 698
 If you concluded the document chart as explained over, you can also present that to regulation enforcement. Later, if you are trying to find lawful motion, you or your attorney can use this chart and its attachments to produce a declaration in aid of your claim. If so, you will have to have to check with all those on the web company companies to conserve that proof for later use. Please notice that CCRI does not endorse or make suggestions regarding any unique services. one. Note that even though you can typically obtain IP handle and other log facts with a subpoena, a law known as the Stored Communications Act, 18 U.S.C. For even further reading on the Stored Communications Act, see Orin S. Kerr, A User’s Guide to the Stored Communications Act — and a Legislator’s Guide to Amending It, 72 Geo. We worked with a handful of tech companies to make this phase-by-phase manual for image consider-down requests. He’s only achieved two of them in human being, even though absolutely nothing sexual happened, and he commonly doesn’t give out his cellular phone range, even with several requests. I am hoping to give a contribution & support other consumers like its aided me. You might also want details from 3rd get-togethers — like sites and email services suppliers- who could have proof related to your dispute.
If you concluded the document chart as explained over, you can also present that to regulation enforcement. Later, if you are trying to find lawful motion, you or your attorney can use this chart and its attachments to produce a declaration in aid of your claim. If so, you will have to have to check with all those on the web company companies to conserve that proof for later use. Please notice that CCRI does not endorse or make suggestions regarding any unique services. one. Note that even though you can typically obtain IP handle and other log facts with a subpoena, a law known as the Stored Communications Act, 18 U.S.C. For even further reading on the Stored Communications Act, see Orin S. Kerr, A User’s Guide to the Stored Communications Act — and a Legislator’s Guide to Amending It, 72 Geo. We worked with a handful of tech companies to make this phase-by-phase manual for image consider-down requests. He’s only achieved two of them in human being, even though absolutely nothing sexual happened, and he commonly doesn’t give out his cellular phone range, even with several requests. I am hoping to give a contribution & support other consumers like its aided me. You might also want details from 3rd get-togethers — like sites and email services suppliers- who could have proof related to your dispute.
To choose if this is right for you, you should choose a provider with treatment, with an eye toward cancellation policies and business reviews. These addresses are quickly leased to web buyers for a period of time of time by their online company providers (ISPs). Thus, you can detect an web consumer by inquiring a website for the IP address linked with the information, and then inquiring the IP address’ operator (the ISP) who it was leased to at the time in query. Even if a person else took the graphic and you do not own the copyright, you can even now request a website to eliminate an intimate impression if you did not consent to its distribution. Without My Consent also delivers a sample proof chart so that you can see what a accomplished chart seems like. If there are extra than a few incidents, continue to fill in the Evidence Chart right up until you have documented every single incident. Use Without My Consent’s Evidence Chart: To assistance victims arrange their proof, Without My Consent recommends creating an evidence chart. Additionally, it could be practical to share these associated legislation or these Without My Consent State Guides with your legal professional.
If you would like more facts concerning the copyright and DMCA course of action, the specialist crew at Without My Consent has produced this guide that may be beneficial. First, take into account if you would like to have a sufferer advocate, mate or household member sit with you as an emotionally supportive and useful witness to the dialogue. First, you can lookup for your identify employing a lookup motor, like Google or Bing, to see if any offending product is in the final results. In the US, sufferer advocates can be uncovered in police stations, rape crisis facilities, domestic violence prevention centers, offices of point out attorneys normal, sheriff’s workplaces, and county offices. Victim advocates can help you obtain proof, accompany you to the police or a lawyer’s place of work, figure out how to continue to keep you risk-free, and aid you discover out if you are suitable for a defense purchase in opposition to the man or woman focusing on you. We attempt to maintain these current, although some may perhaps be out of day. Unless asked for in any other case, intermediaries may well not keep details for incredibly extensive (some may perhaps only retain information for a month or two other individuals extended). Intermediaries frequently manage logs of everyone who accesses their methods (for illustration, to post information and facts or ship an e-mail).
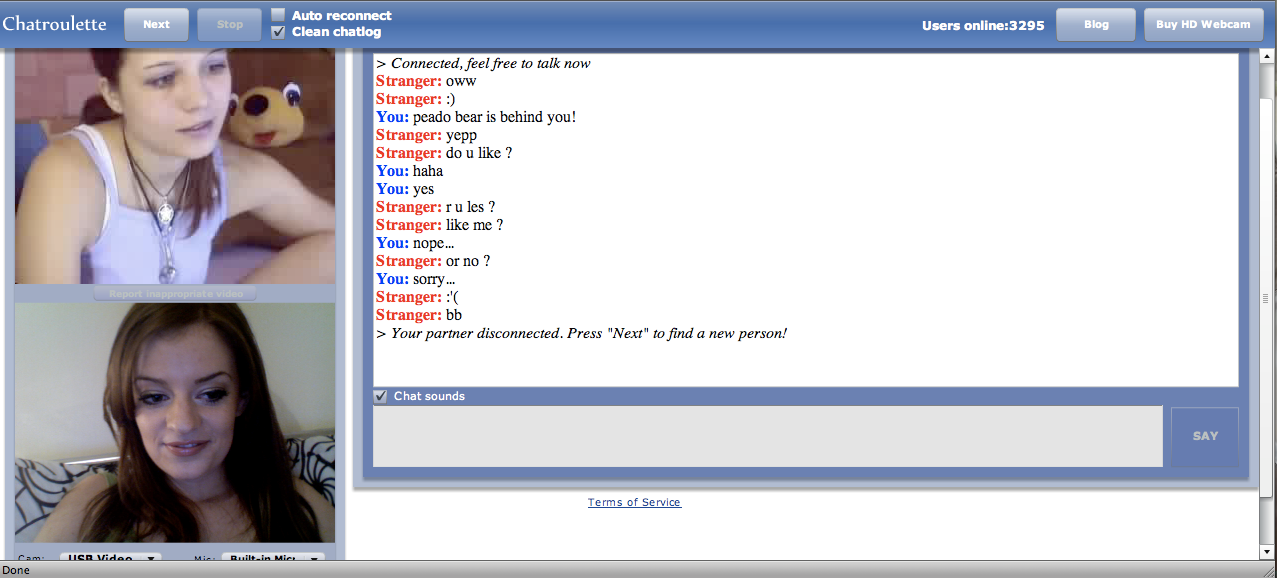
These logs could contain info that can recognize a consumer or provide other vital information and facts, number 1 pornstar together with the day and time a person accessed the site, or the user’s IP address. Site, first acquire some time as properly as examine Lance’s activities. If you are involved about an personal movie, you can just take a screenshot of several frames of the video clip and then use the reverse impression look for operate. one on one movie chat with the product of your choice would make all the change (also regarded as private intercourse chat). If you snapped the photos or took the video clip on your own, you possess the copyright to them. To even more shield you, you can take the further phase and sign-up your pictures with the U.S. Below are a few recommended techniques that you can research for all those photographs. If you are found outdoors of New York, you could lookup on the web for therapists with know-how in digital abuse. One internet site that features this is Google, and their recommendations can be observed here: Reverse Image Search. If you know the condition exactly where the perpetrator resides, you can print that out as very well. You can print out your state’s NCP, sextortion, and/ or deep bogus regulation, or associated regulations, to demonstrate to regulation enforcement that what happened to you is a crime.